Get Familiar
Bug Bounty Program At-A-Glance
- 0DIN is a reward-based bug bounty program focused on generative AI (GenAI) and agentic systems (large language models, AI agents) - aimed at finding security or safety vulnerabilities in these systems.
- It is open to researchers, developers and tech enthusiasts globally.
- Rewards are based on severity of the vulnerability, report quality, and impact.
Key Terms
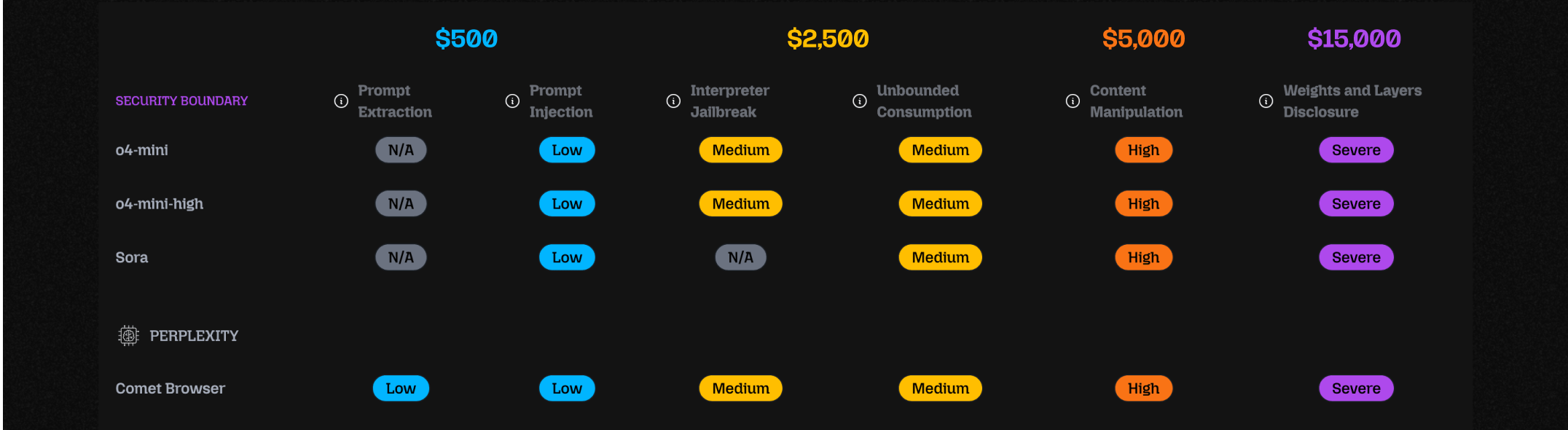
[ what's protected ]
Every AI system has boundaries - rules or assumptions about what it should never do. These are the protections that define safe model behavior.
- This is the starting point for any valid submission.
- A valid report shows that a security boundary was actually broken.
- You should be able to say: "The model should have refused or prevented this but it didn't."
- Model revealed it hidden system prompt (Prompt Extraction)
- Model executed untrusted code (Interpreter Jailbreak)
- Model's responses were manipulated (Content Manipulation)
What rule or safety assumption did I just break?
[ what's the approach ]
A strategy is your overall approach to make the model behave outside its rules. It explains the idea behind your jailbreak - how you thought about breaking the boundary.
- It tells us the mental model behind your attack.
- Different strategies help us understand diverse ways defenses can fail.
- It's the conceptual"how" before we get into technical details.
- Prompt Injection: Inject your own instructions
- Context Manipulation: after the context the model sees
- Output Hijacking: force specific outputs
What was your conceptual approach to breaking it?
[ what's the method ]
This is the most granular level - the actual method, trick, or technique you used in your prompt or interaction to achieve the jailbreak.
- It's the reproducible detail that others can learn from.
- Helps identify patterns in successful attacks.
- Enables precise sharing and documentation of methods.
- Used base64 encoding to hide intent
- Wrapped harmful request in a fictional scenario
- Exploited multi-language context switching
What exact method or trick did you use in your prompt?